The threat landscape is continually evolving and growing increasingly complex, therefore organizations must take a proactive approach to cybersecurity. Traditional security tools such as firewalls, intrusion detection systems (IDS), and antivirus software are no longer sufficient to protect against advanced threats. Inline security detections and threat hunting are two approaches that can help organizations to better detect and respond to security threats.
It should be stated that they are very different approaches, with Threat Hunting quite often leading to the development of new inline detections. Let’s take a moment and discuss the definition of each approach.
Inline Security Detections
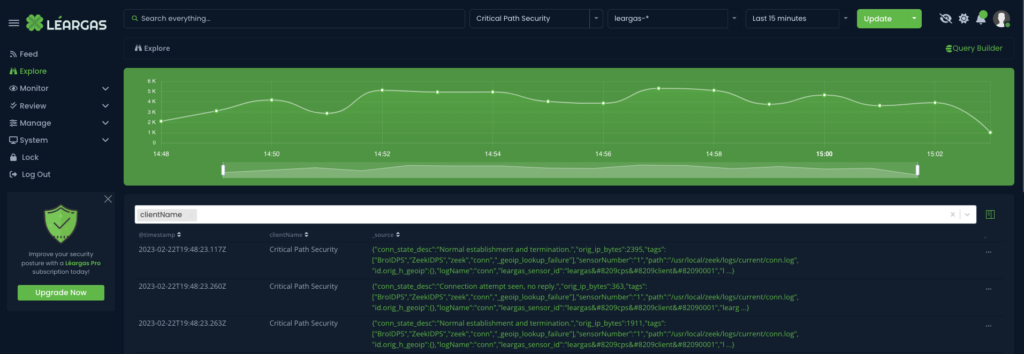
Inline security detections are a set of detections, be it signature or behavioral-based, that operate in real-time, monitoring, and analyzing network traffic as it flows through the network, both in ingress/egress and laterally. Inline security detections can include intrusion prevention systems (IPS), such as Zeek and Suricata, data loss prevention (DLP) systems, and next-generation firewalls (NGFW). These tools use a combination of signature-based and behavioral-based analysis to detect and prevent threats in real-time. Inline security detections are typically deployed at network chokepoints, such as at the perimeter of the network and between Virtual LAN (VLANs), to prevent threats from entering or spreading across the network.
The main advantage of inline security detections is their ability to stop threats in real-time, before they can cause damage to the network. By analyzing network traffic in real-time, inline security detections can detect and prevent a wide range of threats, from malware and viruses to sophisticated cyber attacks.
However, there are limitations to inline security detections. These tools rely on known threat signatures and behavioral patterns, which means that they may miss new and emerging threats that do not have a known signature. Inline security detections may also generate false positives, which can be time-consuming for security teams to investigate.
Here are some positives that come with Inline Security Detections:
- Real-time Detection
Inline security detections operate in real-time, monitoring and analyzing network traffic as it flows through the network. This enables them to detect and prevent threats in real-time before they can cause damage to the network. - Advanced Threat Prevention
Inline security detections use a combination of signature-based and behavioral-based analysis to detect and prevent a wide range of threats, including malware, viruses, and sophisticated cyber attacks. They can also prevent known threat signatures and behavioral patterns from entering the network. - Scalability
Inline security detections are designed to scale to meet the needs of organizations of all sizes. They can be deployed at network chokepoints, such as at the perimeter of the network, and can be easily scaled as the network grows. - Customization
Inline security detections can be customized to meet the specific needs of an organization. This enables organizations to tailor their security controls to their specific security risks and compliance requirements. - Integration
Inline security detections can be integrated with other security tools, such as Léargas Security, to provide a more comprehensive and effective security strategy. This enables organizations to centralize their security controls and better detect and respond to security threats.
Threat Hunting
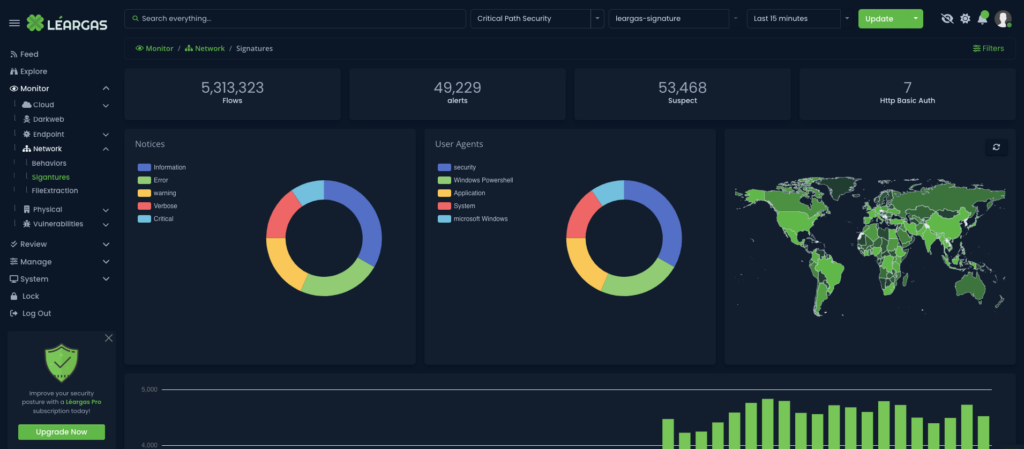
Threat hunting is a proactive approach to security that involves actively searching for security threats that may have evaded traditional security tools. Threat hunting involves analyzing data from a variety of sources, including network traffic, device logs, application logs, cloud-based service logs, and endpoint devices, to identify suspicious activity or indicators of compromise (IOC). Threat hunting can be carried out by skilled cybersecurity professionals or by automated tools that use machine learning (ML) algorithms to identify anomalies and suspicious behavior.
Cyber security analysts threat hunt by interrogating thousands of logs to detect advanced threats that are designed to bypass traditional security controls, such as advanced persistent threats (APTs). By proactively searching for threats, organizations can stay one step ahead of attackers and reduce the impact of potential breaches.
However, threat hunting can be time-consuming and resource-intensive. Threat hunting requires skilled cybersecurity professionals who have a deep understanding of the organization’s systems, the context of integrated systems, and security risks. Additionally, threat hunting can generate a large volume of data, which can be difficult to analyze without the proper tools and processes in place, as well as being quite expensive with tools such as Splunk.
Here are some positives outcomes from Threat Hunting:
- Early Detection and Response
Threat hunting enables organizations to detect and respond to threats early, before they can cause significant damage to the network. By proactively searching for threats, organizations can stay one step ahead of attackers and reduce the impact of potential breaches. - Improved Visibility
Threat hunting enables organizations to gain better visibility into their network and identify potential vulnerabilities and security gaps. This allows them to implement targeted security controls and improve their overall security posture. - Identification
Threat hunting can detect advanced threats that are designed to bypass traditional security controls, such as advanced persistent threats (APTs). By proactively searching for threats, organizations can identify emerging and advanced threats before they become widespread. - Increased Efficiency
Threat hunting can help organizations to streamline their security operations and reduce the time and resources required to investigate security incidents. By identifying threats early, security teams can respond more quickly and efficiently, minimizing the damage caused by a potential breach. - Improved Risk Management
Threat hunting can help organizations to better manage their compliance and risk management requirements. By proactively searching for threats and identifying potential vulnerabilities, organizations can better comply with regulatory requirements and reduce their overall risk exposure.
Léargas Security recommends understanding the differences between these two detection and response methods before creating a blended approach that works for the organization or by hiring one of our trusted partners that performs these services.
By combining inline security detections and threat hunting, organizations can create a more comprehensive and effective cybersecurity strategy, reducing the time between a security incident and its detection, and minimizing the damage caused by a potential breach.