Platform Features

North, South, East & West
Strategically positioned in the core switch utilizing a span port, Léargas XDR not only tracks network flows coming in and out through the firewall, but also watches internal network flows for lateral movement between endpoints, a technique used by threat actors in search of valuable information and business critical assets.

Enrichment
Léargas leverages both Zeek and Suricata Intrusion Detection Systems (IDS) and correlates the results with logs from cloud services such as Duo, Okta, Microsoft, Google, Amazon, and other endpoint data. These results are then extended with data points from curated threat intelligence feeds, geo-location details, known malicious sources, and file hashes, which are then processed to identify anomalies and trends.

Whats This?
With an expanding security landscape knowing it all can be daunting. Léargas has taken steps to fill the knowledge gap by integrating large language models directly into the platform providing a quick and easy reference to help sharpen skills, improve analyst effectiveness, and make better use of time.
File Extraction
With direct packet level access to network flows, Léargas captures and sandboxes potentially dangerous file types on the fly for malware analysis.

Dark Web Scans
Léargas continuously scans both the clear and dark web, following links to otherwise unpublished TOR URLs on the lookout for potential data leaks of private information being shared or sold.

Vulnerability Scans
Léargas also provides access to monthly built network vulnerability scans to provide you with the insight needed to close any gaps before they become targets.
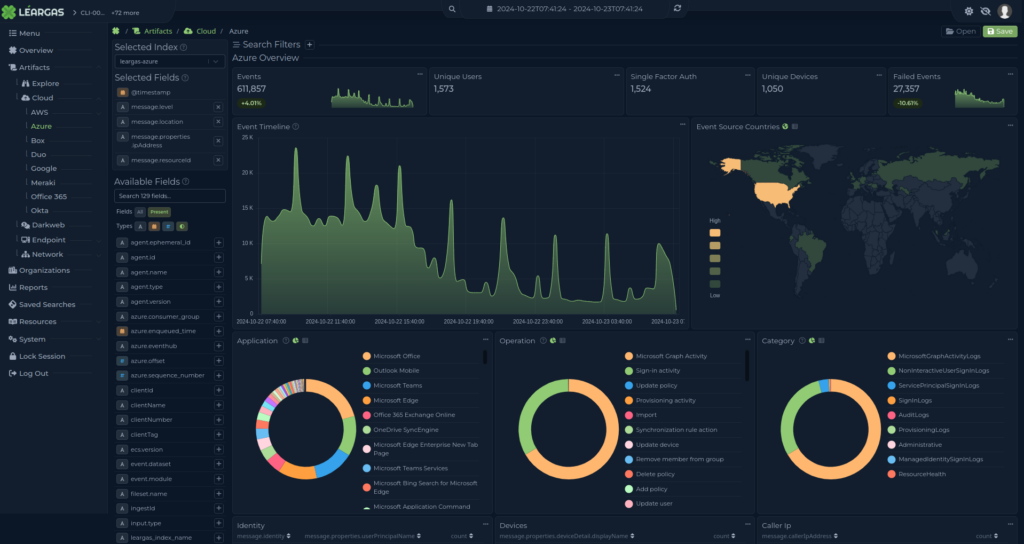
Léargas XDR Cloud Support













Industrial Control Systems Support