With CISA and the FBI under heightened scrutiny from Congress to protect critical infrastructure, the stakes have never been higher in securing U.S. networks from nation-state threats like ‘Salt Typhoon.’ This Chinese-linked threat actor has targeted major telecom providers, underscoring vulnerabilities in the very communications infrastructure that underpins both daily life and national security.
Here is how we can help.
Our security platform is uniquely positioned to help critical infrastructure owners and operators meet this urgent call to action. Below, we detail how our platform’s capabilities align with CISA’s strategic priorities in the face of PRC-backed cyber activities.
1. Comprehensive Threat Intelligence and Anomaly Detection
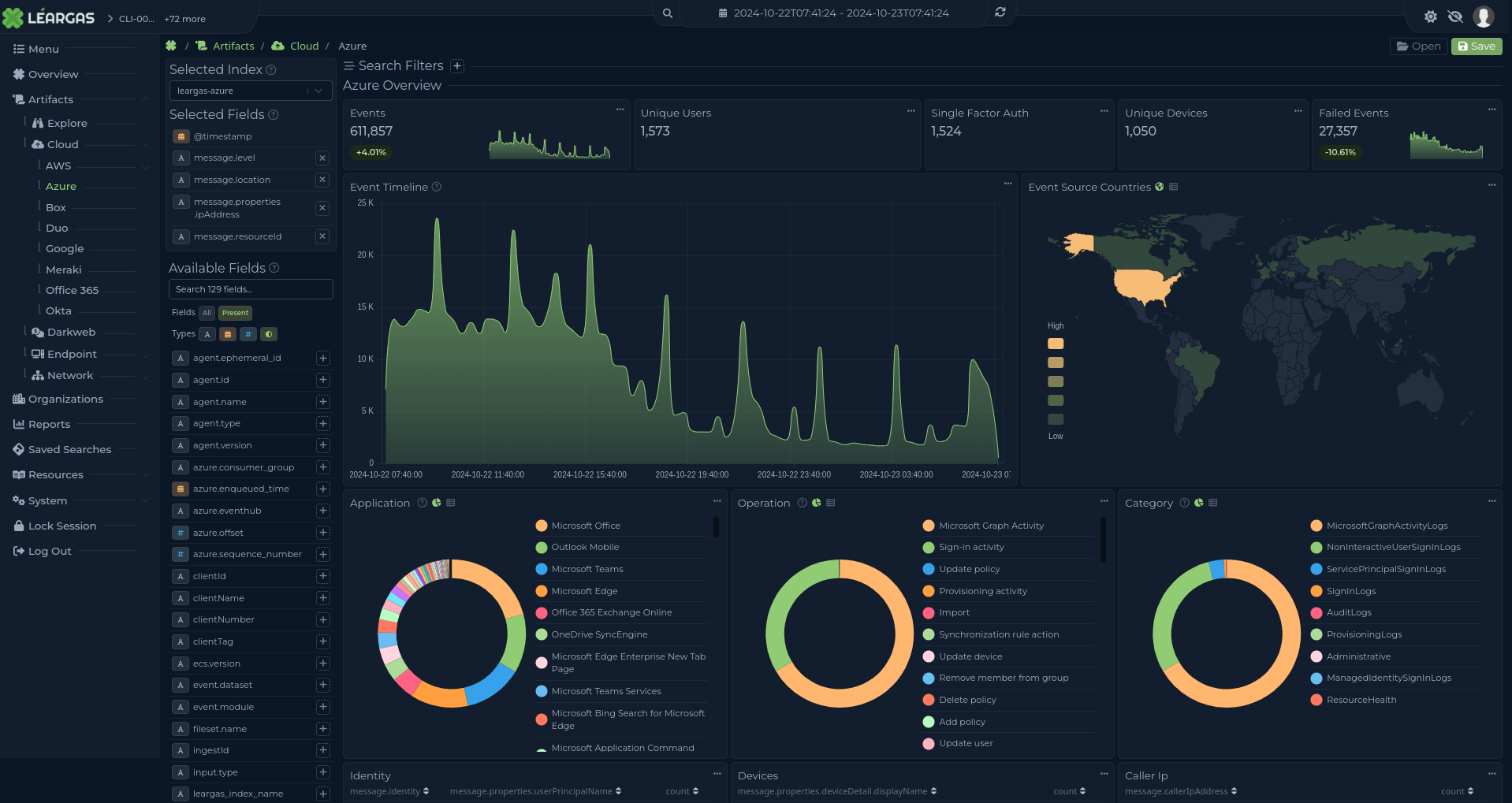
The ability to detect early indicators of advanced persistent threats (APTs) is central to thwarting actors like Salt Typhoon. Our platform leverages AI-driven threat intelligence, enabling real-time analysis of data from global feeds and local monitoring to identify unusual activity patterns. This continuous, automated surveillance is vital to intercepting espionage attempts and mitigating network infiltration risks—a capability that complements CISA’s request for proactive defense mechanisms across critical sectors.
2. Vulnerability Management and Patch Coordination
Given that Salt Typhoon has exploited vulnerabilities within major telecom systems, regular, prioritized vulnerability management is essential. Our platform provides a robust patching protocol that proactively identifies and remediates vulnerabilities across infrastructure before they’re exploited. In line with CISA’s directive, this capability bolsters cyber resilience by ensuring critical systems remain fortified against evolving threats.
3. Endpoint Protection and User Access Control
Nation-state actors often gain access through compromised credentials. Our platform’s endpoint protection and multifactor authentication capabilities ensure that only verified personnel can access sensitive systems. We prevent unauthorized access, which is particularly critical for sectors vulnerable to espionage, such as telecommunications. This aligns with CISA’s push to enhance access control and minimize exposure to potential intelligence gathering.
4. Incident Response and Forensic Capabilities
CISA’s formation of an “emergency team” in response to Salt Typhoon highlights the need for coordinated incident response. Our platform’s robust incident response framework facilitates swift analysis and containment of threats, minimizing downtime and exposure. Coupled with forensic capabilities, it enables a thorough investigation, supporting stakeholders in understanding and mitigating the impacts of breaches.
5. Security Awareness and Compliance
A core tenet of CISA’s mission is to educate infrastructure operators about risks. Our platform provides tailored security training modules and compliance monitoring tools that support adherence to national standards, such as those recommended by CISA. By equipping teams with up-to-date knowledge on evolving tactics from actors like Salt Typhoon, we help enhance cyber vigilance across every user and endpoint.
6. Network Traffic Analysis and Anomaly Detection
Salt Typhoon’s alleged ability to reroute internet traffic showcases the need for robust network traffic analysis. Our platform’s in-depth traffic monitoring allows detection of suspicious redirection attempts and anomalies that could indicate interception or espionage activities. Through real-time alerting and automatic responses, we provide an additional layer of security to combat interference in communications, ensuring data integrity and reliability.
Moving Forward with CISA’s Vision
CISA’s recent “China Threat Snapshot” calls for an empowered, informed, and cyber-resilient America. Our platform offers the technical depth and agility needed to help organizations achieve the cybersecurity resilience that CISA envisions. As we continue to innovate and adapt to the challenges of today’s threat landscape, we remain committed to supporting our nation’s critical infrastructure in identifying, mitigating, and responding to sophisticated cyber threats.