Patrick Kelley, CEO of Léargas Security, will be a featured speaker at the 2024 MRO Security Conference, scheduled to take place on October 1-2, 2024, in St. Paul, Minnesota. This annual conference brings together experts in the energy and security sectors to discuss pressing issues in cybersecurity, particularly as they relate to the protection of critical infrastructure.
Continue readingWhy Léargas is the Smart Choice for Cybersecurity
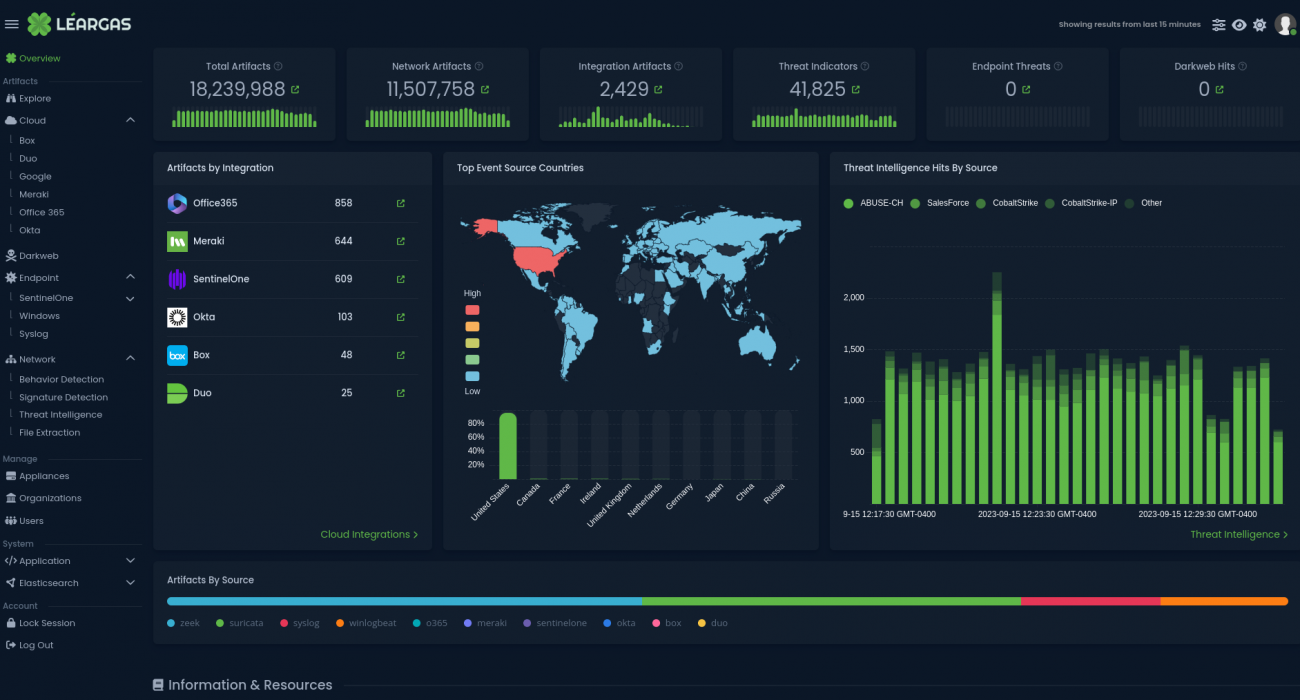
When it comes to cybersecurity, companies often face a tough choice: invest heavily in multiple solutions or opt for a streamlined, cost-effective approach. Enter Léargas, a game-changer in the industry that offers comprehensive cybersecurity services at a fraction of the cost of traditional solutions.
Continue readingRace Report: EuroNASCAR PRO Round 9 at Autodrom Most, Czech Republic
The 2024 NASCAR Whelen Euro Series season finale at Autodrom Most, Czech Republic, presented a weekend full of challenges and perseverance for Ryan Vargas and the Leargas Security team. Despite a tough start during practice, where the team battled a persistent tight-center handling issue due to a failing left-front shock, the crew’s dedication and hard work set the stage for a remarkable comeback.
Continue readingEmpowering Cybersecurity: A Special Workshop by Patrick Kelley at E-ISAC’s CRISP
We are thrilled to announce that our founder, Patrick Kelley of Léargas Security, will be leading a profound workshop titled “In the Trenches of Cybersecurity: A Practical Guide to Incident Response” at the forthcoming Cybersecurity Risk Information Sharing Program (CRISP) event hosted by E-ISAC. This event is scheduled for May 14th in Chicago, IL, and is set to be an essential learning opportunity for cybersecurity experts.
Continue readingAnnouncing Our New Promo Video Reel: Showcasing Léargas’s Comprehensive Security Solutions
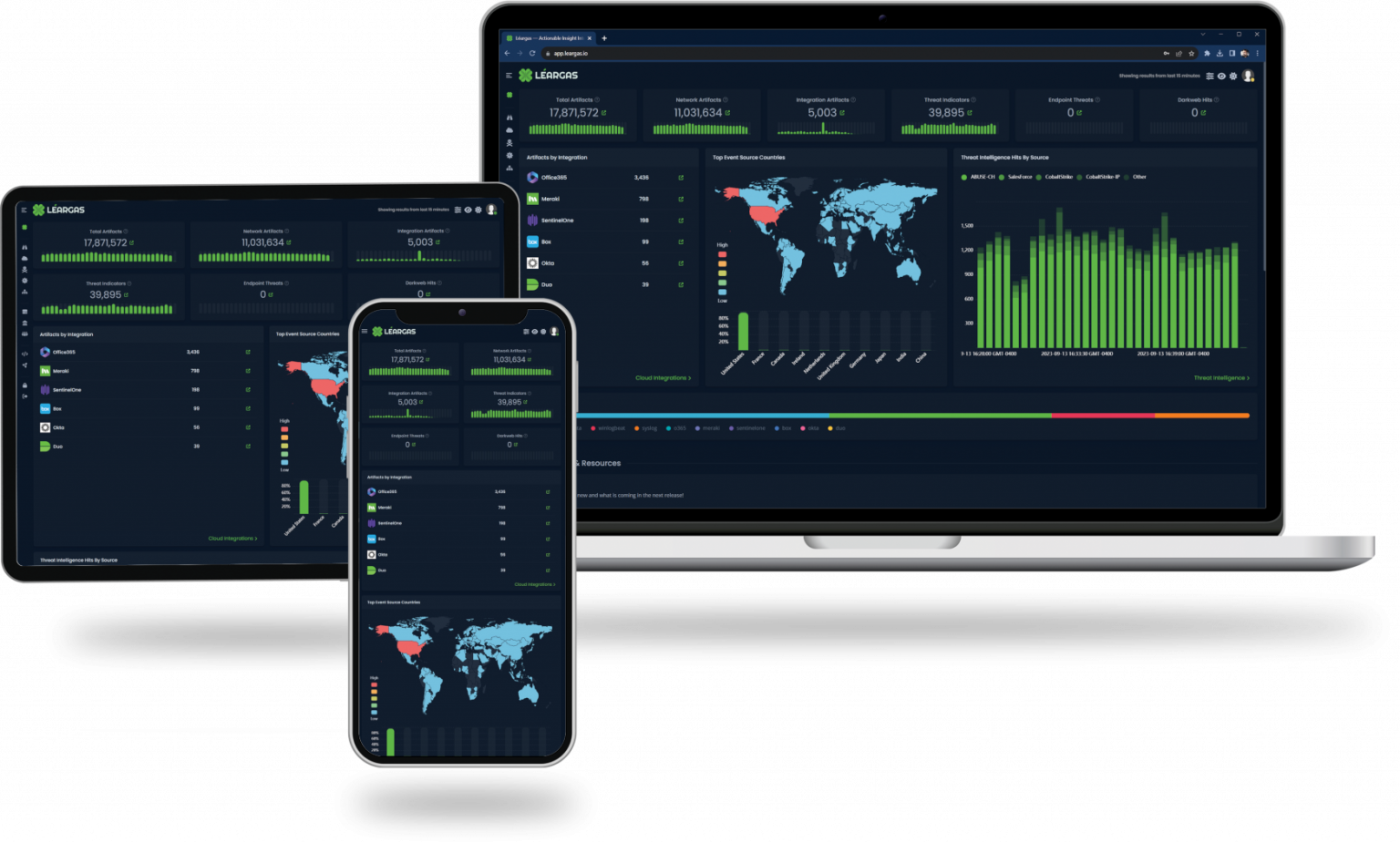
We are thrilled to unveil our latest promotional video reel, designed to highlight the powerful and versatile capabilities of the Léargas platform. This new video encapsulates our commitment to delivering cutting-edge security solutions that seamlessly integrate with traditional on-premise systems, cloud environments, and Industrial Control Systems (ICS).
Continue readingRyan Vargas Claims First Euro Series Podium, Leads 3F Racing and Léargas Security Racing to Top Team Honors
After a 5-year wait, the Euro series finally returned to racing on an oval. The anticipation leading up to this weekend’s races was unlike anything seen before in NASCAR on this side of the Atlantic. Many wondered if the event would meet the high expectations, and those concerns were quickly dispelled by a thrilling NASCAR 2 race on Saturday, delivering an unforgettable experience for the fans.
Continue readingEnhancing Cybersecurity in the Renewable Energy Sector: A Comprehensive Solution from Leargas Security
As the US renewable energy industry expands, it faces increased risks from malicious cyber actors aiming to disrupt power generating operations, steal intellectual property, or ransom critical information. The FBI’s recent Private Industry Notification highlights the urgency for robust cybersecurity measures in this sector. At Leargas Security, we are committed to safeguarding this crucial industry with our comprehensive, scalable cybersecurity platform.
Continue readingAnnouncing Patrick Kelley’s Speaking Engagements for the Second Half of 2024
We are thrilled to announce that Patrick Kelley, CEO of Leargas Security, will be presenting at several prestigious cybersecurity conferences throughout the latter half of 2024. With over 30 years of experience in the field, Patrick is set to share his extensive knowledge and insights on various critical topics.
Continue readingExciting New Features in Léargas v0.1.0-beta.4
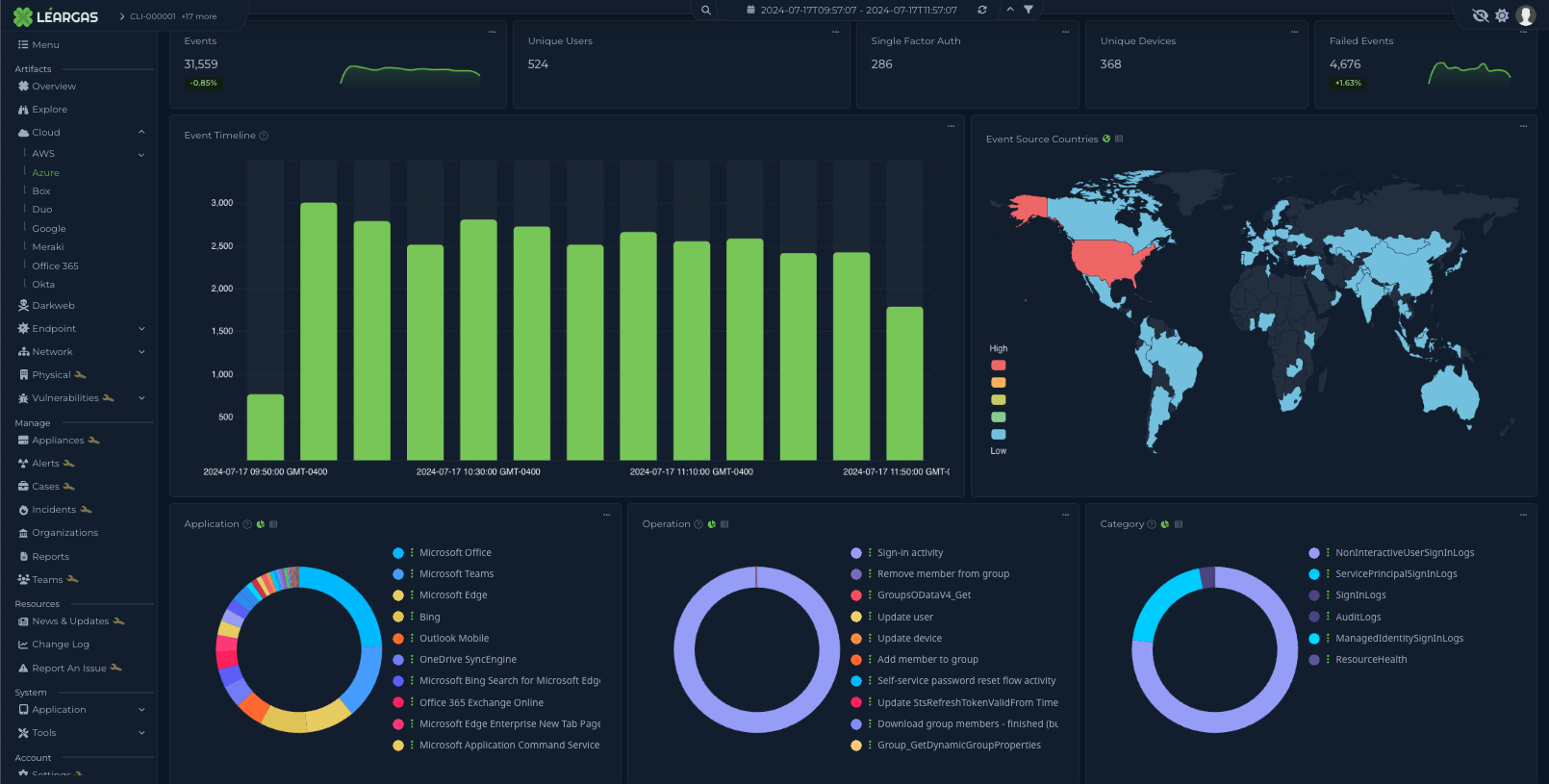
We are thrilled to announce the upcoming release of Léargas v0.1.0-beta.4! This update introduces several significant enhancements and new features aimed at improving user experience, security, and operational efficiency across the platform. Here’s a sneak peek into what’s new: Switching between devices has never been easier. With multi-device session support, you can effortlessly continue your sessions without any disruptions, providing convenient access to Léargas from anywhere. This feature enhances user experience by ensuring seamless transitions across devices.
Continue readingStrengthening the Fort: A New Era of Streamlined Cyber Incident Reporting
In the ever-evolving landscape of cybersecurity, the necessity for clear channels of communication and collaboration cannot be overstated. That’s why the recent announcement from the US Department of Homeland Security (DHS) is a crucial step forward for the community at large. On Tuesday, the DHS released an influential document that aims to revolutionize how federal agencies approach cyber incident reporting, ushering in a more harmonized and efficient system that stands to benefit critical infrastructure entities immensely.
Continue reading