When it comes to cybersecurity, companies often face a tough choice: invest heavily in multiple solutions or opt for a streamlined, cost-effective approach. Enter Léargas, a game-changer in the industry that offers comprehensive cybersecurity services at a fraction of the cost of traditional solutions.
Continue readingEnhancing Cybersecurity in the Renewable Energy Sector: A Comprehensive Solution from Leargas Security
As the US renewable energy industry expands, it faces increased risks from malicious cyber actors aiming to disrupt power generating operations, steal intellectual property, or ransom critical information. The FBI’s recent Private Industry Notification highlights the urgency for robust cybersecurity measures in this sector. At Leargas Security, we are committed to safeguarding this crucial industry with our comprehensive, scalable cybersecurity platform.
Continue readingStrengthening the Fort: A New Era of Streamlined Cyber Incident Reporting
In the ever-evolving landscape of cybersecurity, the necessity for clear channels of communication and collaboration cannot be overstated. That’s why the recent announcement from the US Department of Homeland Security (DHS) is a crucial step forward for the community at large. On Tuesday, the DHS released an influential document that aims to revolutionize how federal agencies approach cyber incident reporting, ushering in a more harmonized and efficient system that stands to benefit critical infrastructure entities immensely.
Continue readingLéargas XDR – Defending America’s Critical Infrastructure
In 2014, the pressing need for a comprehensive cybersecurity solution to the vulnerabilities faced by nearly 900 electric cooperatives was acknowledged by the U.S. Department of Energy (DOE). Understanding that the integration of Extended Detection and Response (XDR) solutions in electric cooperatives has become increasingly important in recent years, Léargas was driven to create a versatile and cost-effective platform. As these cooperatives digitally transform and adopt modern technologies, they also become more vulnerable to sophisticated cyber threats. These potential attacks not only pose a risk to the integrity of the cooperatives’ data, but also threaten the stability of the electrical grid that powers our communities.
Continue readingThe Crucial Role of Zeek-based Platforms like Leargas Security XDR in IT and OT Environments
The fusion of Information Technology (IT) and Operational Technology (OT) ecosystems is increasingly becoming integral in today’s enterprises. As the cyber threat landscape continues to evolve, posing intricate and sophisticated attacks, organizations are turning to advanced security solutions such as Leargas Security XDR. This potent platform, built on the robust Zeek framework, offers an all-in-one approach to securing IT and OT environments, providing vital insights and capabilities that help businesses stay ahead of potential threats. This article will delve into the significance of Zeek-based solutions like Leargas Security XDR with an emphasis on OT protocol analysis including DNP3, Modbus, and S7.
Continue readingRevolutionizing Energy Cooperatives: The Value of Leargas Security XDR
As the globe becomes progressively dependent on digital systems and automation, cybersecurity has evolved into a pressing issue for all organizations. This trend is not just applicable to major corporations or tech firms; it is equally relevant to entities like energy cooperatives. Given their key responsibility in delivering vital services to communities, these cooperatives cannot afford to overlook the importance of robust cybersecurity measures.
Continue readingLeveraging CIRCL’s AIL Framework and Leargas Security XDR Platform for Effective Breach Discovery and Management
As the digital landscape expands, so does the complexity and magnitude of cybersecurity threats. This shift has led to the development of sophisticated cybersecurity tools designed to detect, manage, and respond to potential security breaches. Two such tools making waves in the cybersecurity field are the Computer Incident Response Center Luxembourg (CIRCL) Analysis Information Leak (AIL) framework and the Leargas Security Extended Detection and Response (XDR) platform.
Continue readingLéargas Security with AI: The Cost Factor
With the increasing number of cyber-attacks and the ever-changing threat landscape, there is a growing demand for cybersecurity analysts who can effectively protect computer systems and networks. However, the shortage of skilled cybersecurity professionals is a major challenge that many organizations face. Artificial Intelligence (AI) has emerged as a potential solution to this problem, and its importance in the strategic shortening of skills gaps in cybersecurity analysts cannot be overstated. That is why Léargas Security has leveraged ChatGPT for strategically shortening the knowledge gap.
Continue readingInline Detections and Hunting: The Differences and Value Gained
The threat landscape is continually evolving and growing increasingly complex, therefore organizations must take a proactive approach to cybersecurity. Traditional security tools such as firewalls, intrusion detection systems (IDS), and antivirus software are no longer sufficient to protect against advanced threats. Inline security detections and threat hunting are two approaches that can help organizations to better detect and respond to security threats.
Continue readingCorrelation and Enrichment: Office365 and Endpoint Security
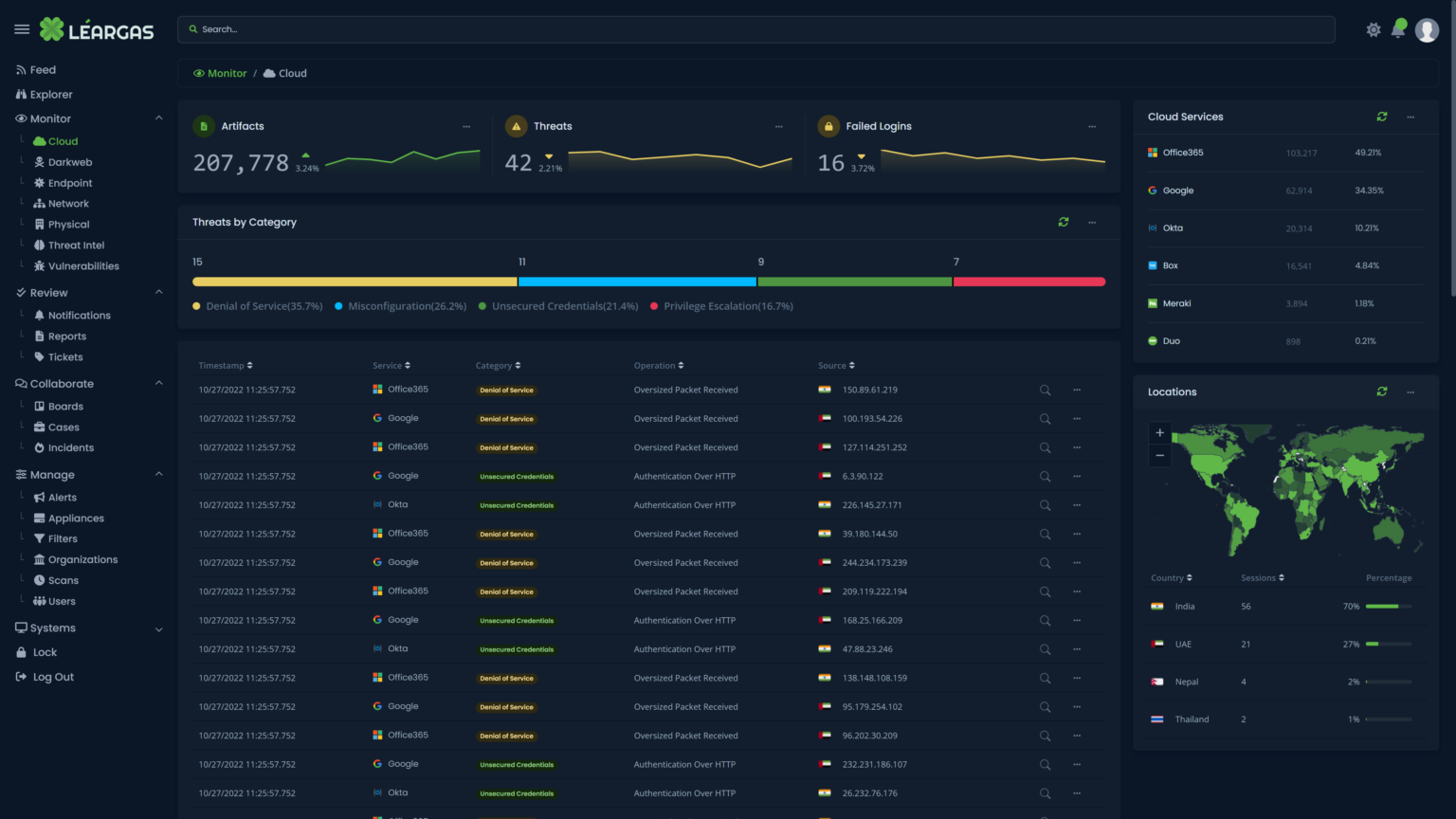
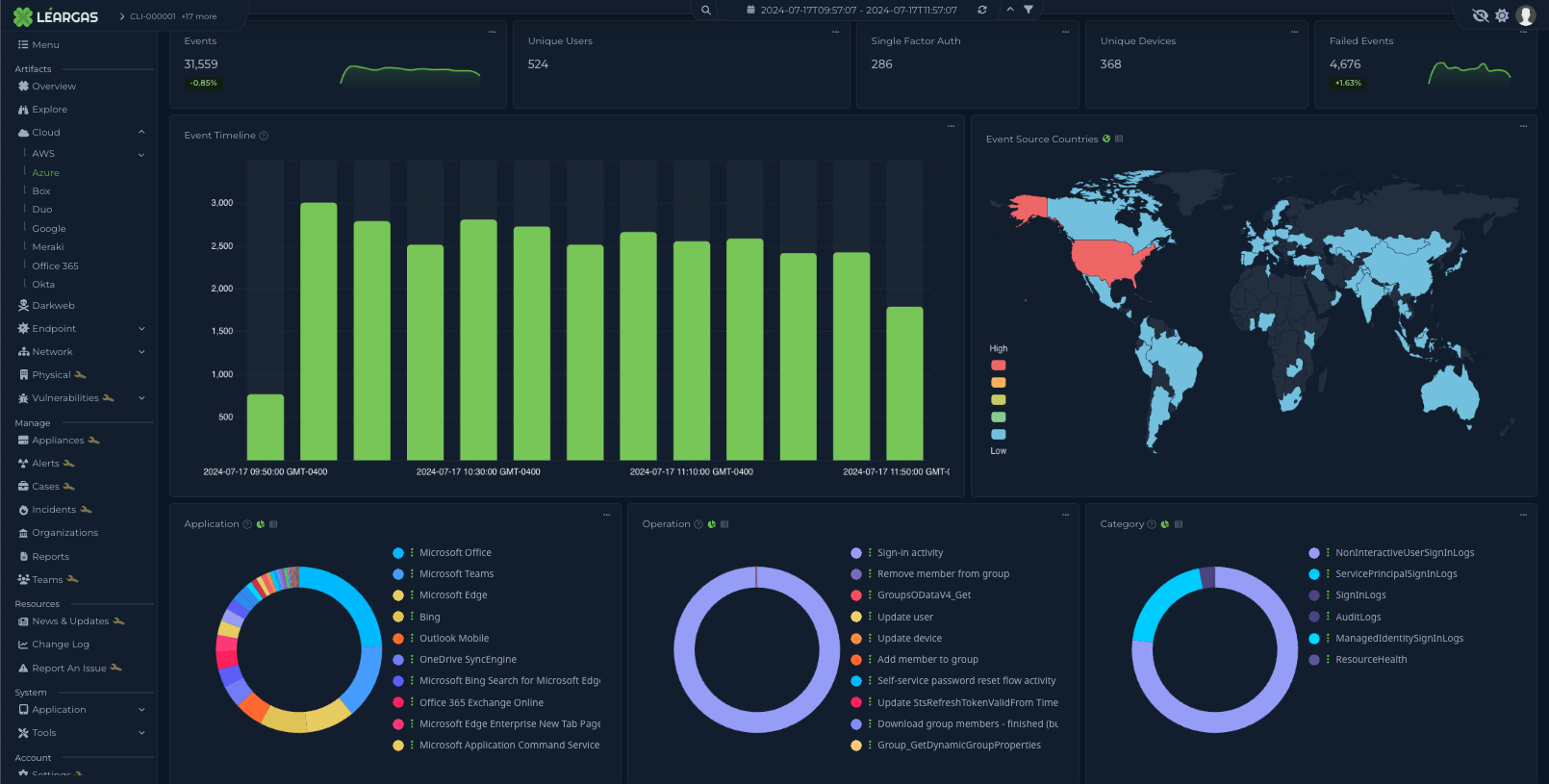
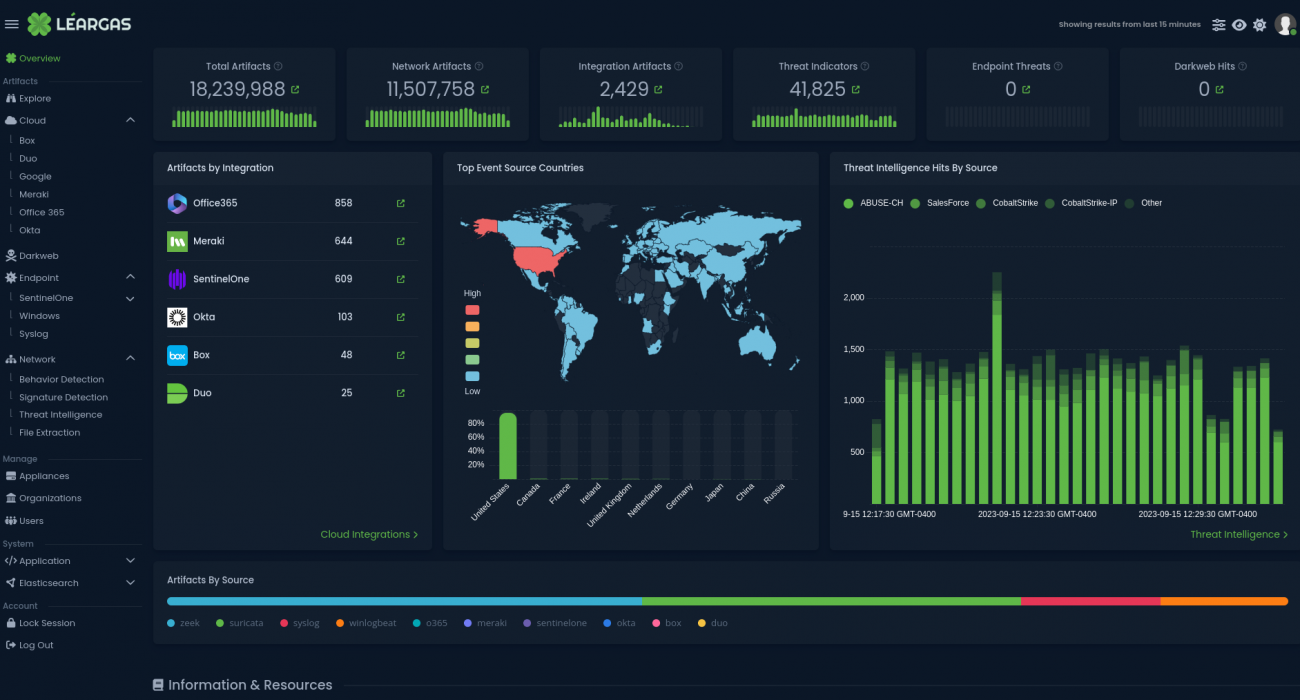
As organizations increasingly rely on cloud-based services such as Office 365 for their productivity and collaboration needs, it’s critical to understand the importance of correlating logs from both the cloud service and the endpoint devices. This correlation can provide a comprehensive view of the activities taking place within the organization and help ensure the security and compliance of sensitive information, no matter where the endpoint might be.
One of the main benefits of correlating Office 365 and Endpoint Security logs is that it can help identify suspicious or malicious activity. For example, if a user’s endpoint device shows signs of a security breach, geographically-impossible authentication attempts, or attacks such as a virus or malware event, the corresponding Office 365 logs can provide valuable information on what data may have been accessed or exfiltrated.
The Léargas Security platform automatically correlates the data from the sources into single searches and alerts.
Additionally, correlating Office 365 and Endpoint Security logs can also help organizations identify compliance violations, such as unauthorized access to sensitive information. With the right tools, organizations can quickly identify when a user has taken actions that violate their data protection policies, such as downloading confidential data onto a personal device or sending sensitive information to an unauthorized email recipient.
Moreover, correlating logs can help improve incident response time. In the event of a security incident, having a comprehensive view of the activities that took place can help organizations quickly identify the source and scope of the problem, enabling them to respond and resolve the issue more efficiently.
Here are the Top 10 reasons for automatically correlating Office 365 and Endpoint Security logs:
- IMPROVED VISIBILITY INTO USER ACTIVITY: Correlating logs provides a comprehensive view of what users are doing within the organization, including access to sensitive information and email correspondence, regardless of location and time.
- DETECTING SUSPICIOUS OR MALICIOUS ACTIVITY: Correlating logs can help identify potential security threats and unauthorized access to sensitive data.
- IMPROVING INCIDENT RESPONSE TIME: Having a comprehensive view of activities can help organizations quickly identify the source and scope of security incidents, allowing them to respond more efficiently.
- ENSURING COMPLIANCE WITH INDUSTRY REGULATIONS: Organizations can use log data to demonstrate compliance with regulations such as GDPR and HIPAA.
- AUDITING AND COMPLIANCE REPORTING: Log data can provide valuable insights for auditing and compliance reporting, helping organizations ensure that their security and privacy practices are up to standards.
- PROTECTING SENSITIVE DATA: Correlating logs can help organizations identify when sensitive data is being accessed, downloaded, or sent to unauthorized recipients, allowing them to take appropriate action to protect it.
- DETECTING ENDPOINT SECURITY BREACHES: Endpoint devices are a common target for attackers, and correlating logs can help organizations identify when a device has been compromised and what data may have been accessed.
- IDENTIFYING UNUSUAL USER BEHAVIOR: Correlating logs can help organizations identify when users are engaging in suspicious or unusual behavior, allowing them to take appropriate action to mitigate potential threats.
- DETECTING DATA EXFILTRATION: By tracking user activities, organizations can identify when sensitive data is being exfiltrated and take appropriate action to prevent it.
- ENHANCING SECURITY AND PRIVACY: By correlating logs, organizations can gain a better understanding of their security and privacy practices and take appropriate steps to improve them.
Finally, correlating Office 365 and Endpoint Security logs can also provide valuable insights for auditing and compliance reporting. Organizations can use the data from these logs to demonstrate their compliance with industry regulations and standards, such as GDPR and HIPAA, by providing a detailed view of their security and privacy practices.