Léargas Security, a leading cybersecurity firm, has made a name for itself by providing top-notch security solutions and services to clients worldwide. With a focus on innovation, Léargas Security stays ahead of emerging threats by continuously updating its strategies and techniques. The company’s dedication to excellence has made it the perfect partner for NRECA in the 2023 Co-Op Cyber Tech Conference.
Continue readingLéargas Security with AI: The Cost Factor
With the increasing number of cyber-attacks and the ever-changing threat landscape, there is a growing demand for cybersecurity analysts who can effectively protect computer systems and networks. However, the shortage of skilled cybersecurity professionals is a major challenge that many organizations face. Artificial Intelligence (AI) has emerged as a potential solution to this problem, and its importance in the strategic shortening of skills gaps in cybersecurity analysts cannot be overstated. That is why Léargas Security has leveraged ChatGPT for strategically shortening the knowledge gap.
Continue readingLeveraging ChatGPT To Close The Knowledge Gaps
Cybersecurity threats are increasingly becoming more frequent, sophisticated, and complex, and companies are struggling to keep up with the pace. With the rise of the internet, the number of attacks has grown exponentially, and attackers are continuously finding new ways to bypass traditional security measures. As a result, the demand for security analysts has increased drastically, however, there is a significant shortage of qualified professionals to fill these positions.
Continue readingWhat Is SecOps and What Is The Value Of SecOps To Organizations?
The Importance of Normalization and Scoring of Threat Intelligence Artifacts
In the present-day, interconnected world, businesses confront an expanding threat landscape. To safeguard themselves from cyber threats, organizations rely on threat intelligence, which is one of the most valuable tools available. However, the effectiveness of threat intelligence hinges on the quality of its data. That’s why normalization and scoring of threat intelligence artifacts are two indispensable procedures that guarantee high-quality data.
Continue readingVisibility and Log Fidelity – Recommendations
Inline Detections and Hunting: The Differences and Value Gained
The threat landscape is continually evolving and growing increasingly complex, therefore organizations must take a proactive approach to cybersecurity. Traditional security tools such as firewalls, intrusion detection systems (IDS), and antivirus software are no longer sufficient to protect against advanced threats. Inline security detections and threat hunting are two approaches that can help organizations to better detect and respond to security threats.
Continue readingAttack Surface Reduction: Why It Matters.
In today’s digital age, cybersecurity is more critical than ever before. With the growing number of cyber threats, it is essential to reduce the attack surface to protect your organization’s assets. What is the “attack surface”? The attack surface refers to the total number of vulnerabilities, entry points, and possible attack vectors that hackers can exploit to gain unauthorized access to an organization’s systems and data. In this blog post, we will discuss the importance of reducing the cybersecurity attack surface and some effective ways to do it.
Continue readingThe Importance of Artificial Intelligence and Machine Learning in Cybersecurity

Léargas Security, like many other Extended Detection and Response (XDR) platforms, has become an essential part of modern cybersecurity. As the number and complexity of cyber threats continue to increase, more organizations are turning to Léargas to provide comprehensive and proactive threat detection and response capabilities. And one of the most significant advancements in the Léargas platform in recent years has been the integration of artificial intelligence (AI) and machine learning (ML) algorithms.
Let’s understand what Léargas is. Léargas is an advanced security platform that provides organizations with a comprehensive approach to threat detection and response. Unlike traditional security solutions that only focus on specific parts of an organization’s infrastructure, the Léargas platform leverages data from multiple security tools and data sources, both on-premises and in the cloud, to provide a more holistic and comprehensive view of the network, endpoints, and cloud environments. The Léargas platform combines security analytics, threat intelligence, and automated response capabilities to detect and respond to threats across the entire infrastructure.
With the integration of artificial intelligence and machine learning, Léargas can improve the detection capabilities and speed up response times for its subscribers. Artificial intelligence and machine learning algorithms can process copious amounts of data from a growing number of sources in real-time, identifying patterns and anomalies that may indicate an attack. This allows the Léargas platform to detect and respond to threats more quickly, reducing the risk of damage and data loss.
So, here are some specific ways that the Léargas platform utilizes AI and ML:
- Enhanced detection capabilities: AI and ML algorithms can analyze large volumes of data from various sources, such as network traffic, logs, and endpoints. This enables Léargas to detect advanced and emerging threats that traditional security solutions may miss.
- Faster response times: AI and ML algorithms can automate response actions, such as isolating infected endpoints, blocking malicious traffic, and containing the attack. This permits Léargas to respond quickly to threats, reducing the time-to-detection and time-to-response.
- Reduced false positives: AI and ML algorithms can filter out false positives, reducing the number of alerts that security teams need to investigate. This saves time and resources, allowing security teams, both MSP (Managed Service Providers), MSSP, and independent organizations to focus on more critical threats.
- Improved threat intelligence: AI and ML algorithms can analyze threat intelligence data, identifying new patterns and trends that may indicate emerging threats. This enables Léargas to stay ahead of the threat landscape, providing proactive threat detection and response capabilities. Additionally, Léargas partners with companies like Critical Path Security to gain more valuable intelligence each day.
- Better risk management: AI and ML algorithms can provide risk scoring and prioritization, allowing security teams to focus on the most critical threats.
- Malware analysis: Machine learning algorithms are used by the Léargas platform and the supported EDR (Endpoint Detection and Response) solutions to analyze malware behavior, identifying patterns that may indicate the presence of malware, ransomware, or an internal threat actor on a network.
Léargas strives to secure organizations by enhancing threat detection capabilities, speeding up response times, reducing false positives, improving threat intelligence, and providing better risk management.
As the threat landscape continues to evolve, organizations need advanced security solutions that can keep pace with the changing threat landscape. The AI-powered Léargas security platform provides a proactive and comprehensive approach to cybersecurity, helping organizations to stay one step ahead of cyber threats.
Correlation and Enrichment: Office365 and Endpoint Security
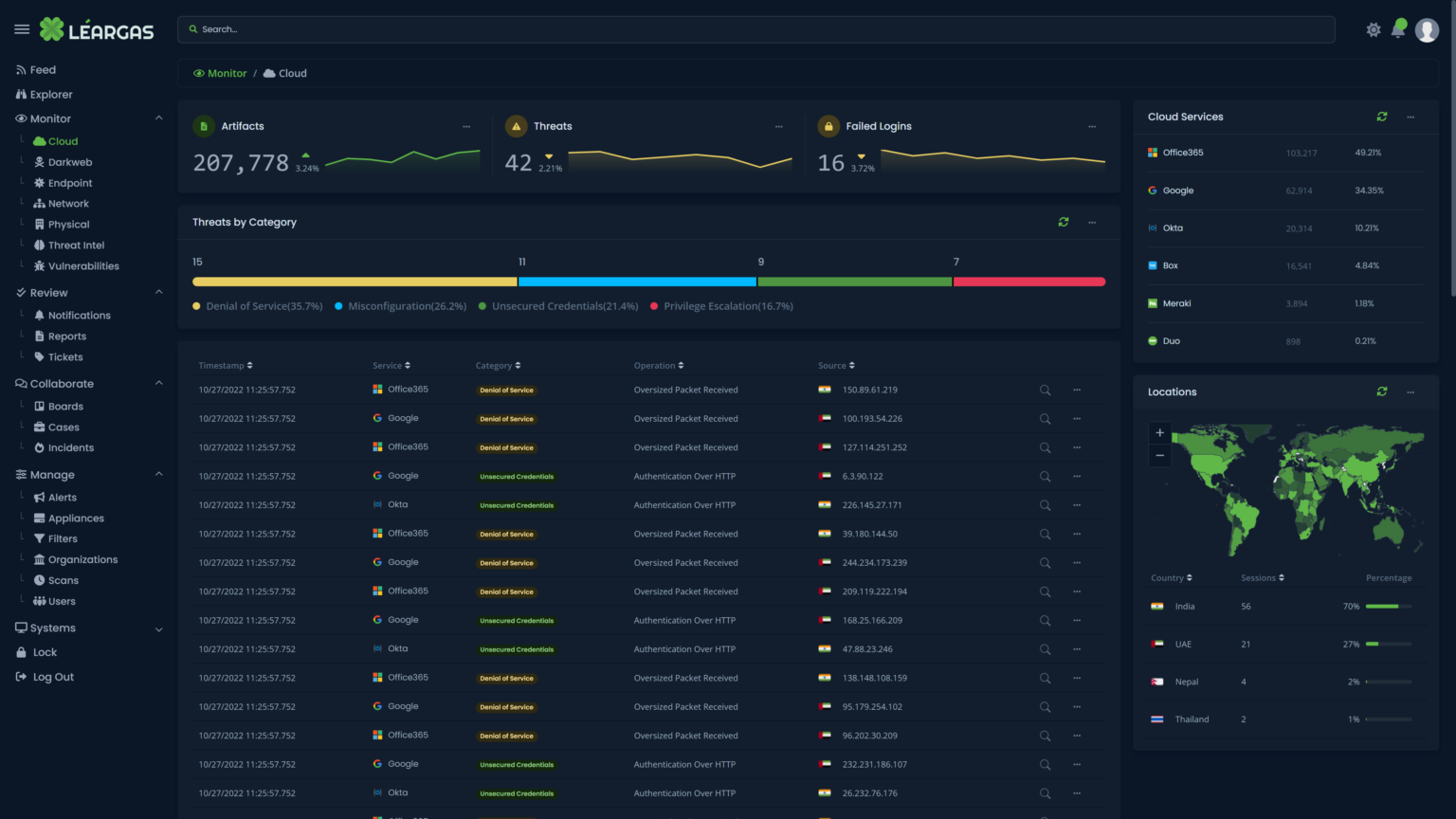
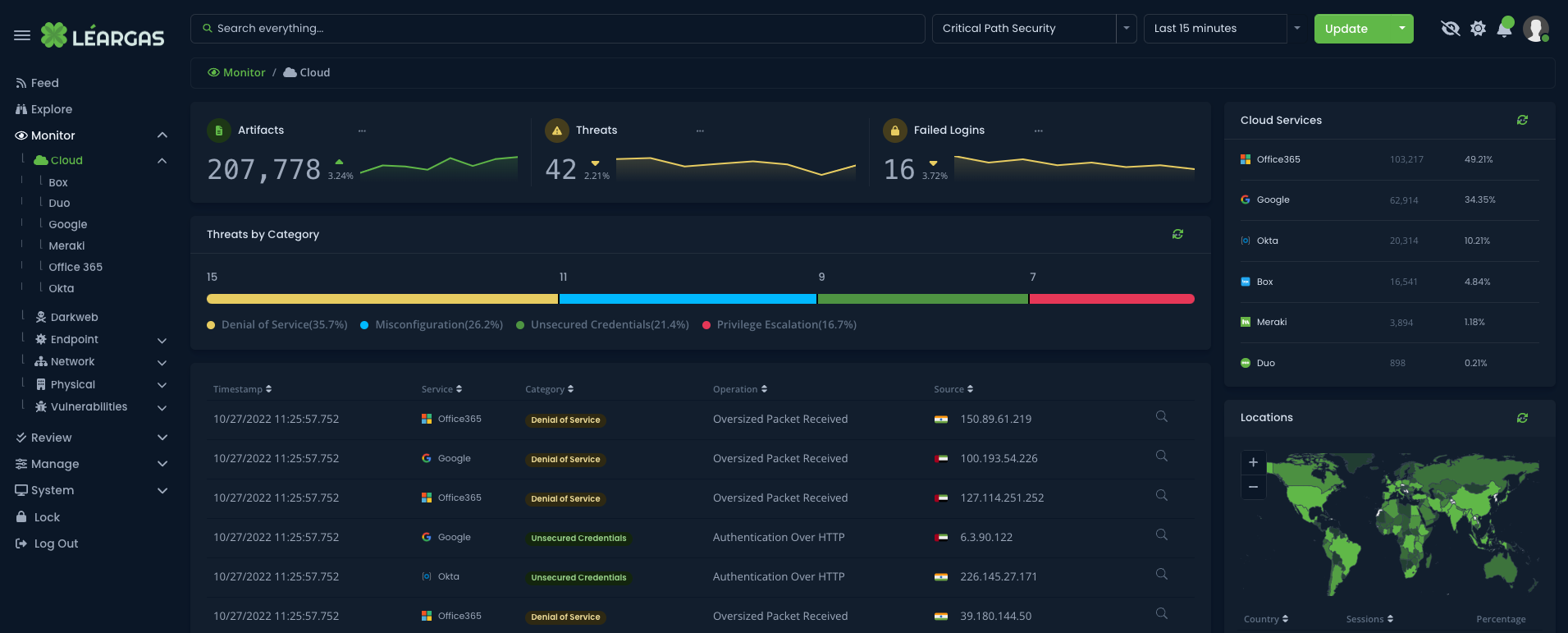
As organizations increasingly rely on cloud-based services such as Office 365 for their productivity and collaboration needs, it’s critical to understand the importance of correlating logs from both the cloud service and the endpoint devices. This correlation can provide a comprehensive view of the activities taking place within the organization and help ensure the security and compliance of sensitive information, no matter where the endpoint might be.
One of the main benefits of correlating Office 365 and Endpoint Security logs is that it can help identify suspicious or malicious activity. For example, if a user’s endpoint device shows signs of a security breach, geographically-impossible authentication attempts, or attacks such as a virus or malware event, the corresponding Office 365 logs can provide valuable information on what data may have been accessed or exfiltrated.
The Léargas Security platform automatically correlates the data from the sources into single searches and alerts.
Additionally, correlating Office 365 and Endpoint Security logs can also help organizations identify compliance violations, such as unauthorized access to sensitive information. With the right tools, organizations can quickly identify when a user has taken actions that violate their data protection policies, such as downloading confidential data onto a personal device or sending sensitive information to an unauthorized email recipient.
Moreover, correlating logs can help improve incident response time. In the event of a security incident, having a comprehensive view of the activities that took place can help organizations quickly identify the source and scope of the problem, enabling them to respond and resolve the issue more efficiently.
Here are the Top 10 reasons for automatically correlating Office 365 and Endpoint Security logs:
- IMPROVED VISIBILITY INTO USER ACTIVITY: Correlating logs provides a comprehensive view of what users are doing within the organization, including access to sensitive information and email correspondence, regardless of location and time.
- DETECTING SUSPICIOUS OR MALICIOUS ACTIVITY: Correlating logs can help identify potential security threats and unauthorized access to sensitive data.
- IMPROVING INCIDENT RESPONSE TIME: Having a comprehensive view of activities can help organizations quickly identify the source and scope of security incidents, allowing them to respond more efficiently.
- ENSURING COMPLIANCE WITH INDUSTRY REGULATIONS: Organizations can use log data to demonstrate compliance with regulations such as GDPR and HIPAA.
- AUDITING AND COMPLIANCE REPORTING: Log data can provide valuable insights for auditing and compliance reporting, helping organizations ensure that their security and privacy practices are up to standards.
- PROTECTING SENSITIVE DATA: Correlating logs can help organizations identify when sensitive data is being accessed, downloaded, or sent to unauthorized recipients, allowing them to take appropriate action to protect it.
- DETECTING ENDPOINT SECURITY BREACHES: Endpoint devices are a common target for attackers, and correlating logs can help organizations identify when a device has been compromised and what data may have been accessed.
- IDENTIFYING UNUSUAL USER BEHAVIOR: Correlating logs can help organizations identify when users are engaging in suspicious or unusual behavior, allowing them to take appropriate action to mitigate potential threats.
- DETECTING DATA EXFILTRATION: By tracking user activities, organizations can identify when sensitive data is being exfiltrated and take appropriate action to prevent it.
- ENHANCING SECURITY AND PRIVACY: By correlating logs, organizations can gain a better understanding of their security and privacy practices and take appropriate steps to improve them.
Finally, correlating Office 365 and Endpoint Security logs can also provide valuable insights for auditing and compliance reporting. Organizations can use the data from these logs to demonstrate their compliance with industry regulations and standards, such as GDPR and HIPAA, by providing a detailed view of their security and privacy practices.