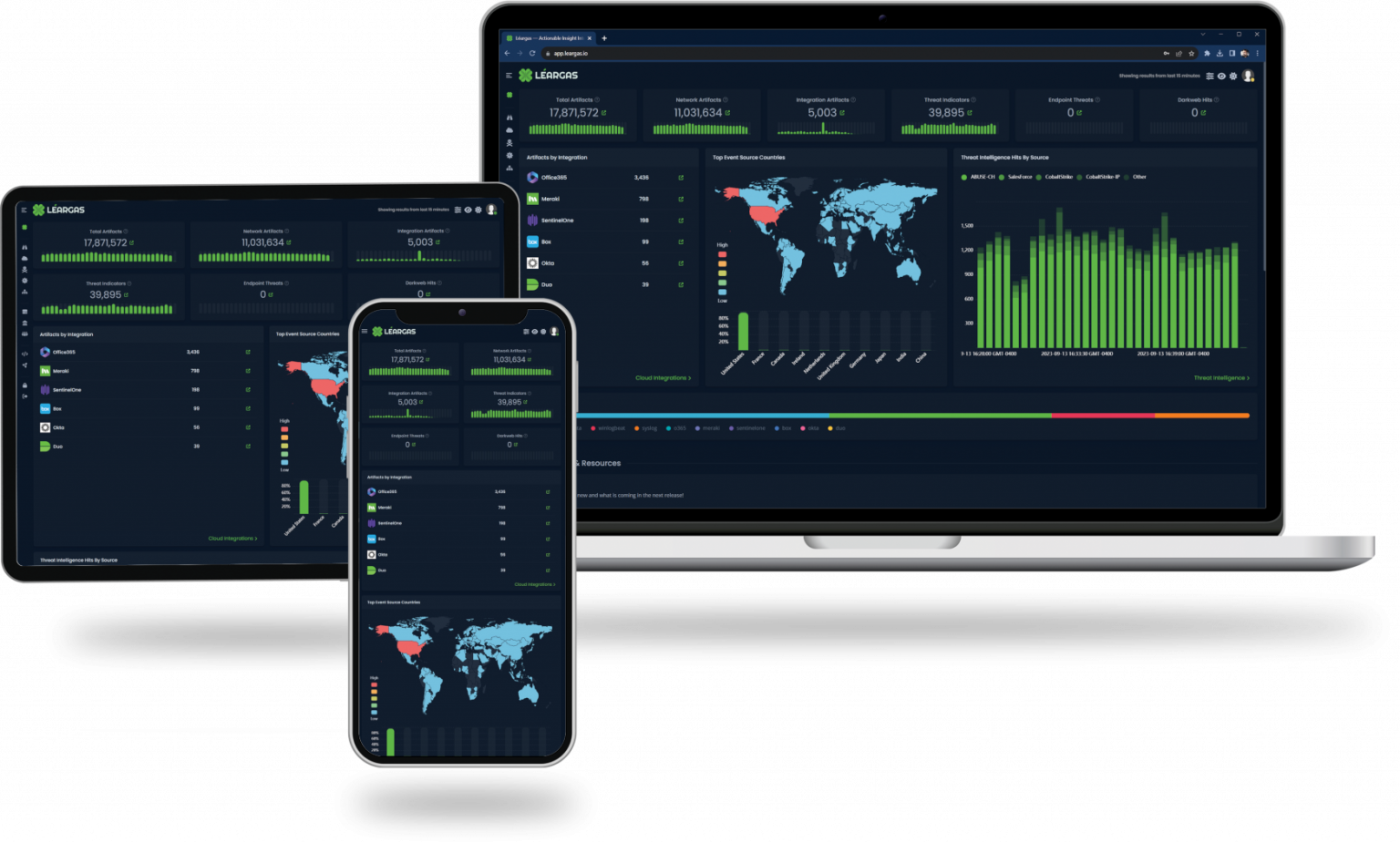
In today’s digital age, safeguarding critical infrastructure is more crucial than ever. However, many organizations are grappling with cybersecurity challenges due to limited budgets, insufficient staffing, and outdated solutions. Enter Léargas-a comprehensive SaaS cybersecurity platform designed to address these pressing issues and revolutionize how critical infrastructure is protected.
Continue readingExciting New Features in Léargas v0.1.0-beta.4
We are thrilled to announce the upcoming release of Léargas v0.1.0-beta.4! This update introduces several significant enhancements and new features aimed at improving user experience, security, and operational efficiency across the platform. Here’s a sneak peek into what’s new: Switching between devices has never been easier. With multi-device session support, you can effortlessly continue your sessions without any disruptions, providing convenient access to Léargas from anywhere. This feature enhances user experience by ensuring seamless transitions across devices.
Continue readingLéargas XDR – Defending America’s Critical Infrastructure
In 2014, the pressing need for a comprehensive cybersecurity solution to the vulnerabilities faced by nearly 900 electric cooperatives was acknowledged by the U.S. Department of Energy (DOE). Understanding that the integration of Extended Detection and Response (XDR) solutions in electric cooperatives has become increasingly important in recent years, Léargas was driven to create a versatile and cost-effective platform. As these cooperatives digitally transform and adopt modern technologies, they also become more vulnerable to sophisticated cyber threats. These potential attacks not only pose a risk to the integrity of the cooperatives’ data, but also threaten the stability of the electrical grid that powers our communities.
Continue readingThe Crucial Role of Zeek-based Platforms like Leargas Security XDR in IT and OT Environments
The fusion of Information Technology (IT) and Operational Technology (OT) ecosystems is increasingly becoming integral in today’s enterprises. As the cyber threat landscape continues to evolve, posing intricate and sophisticated attacks, organizations are turning to advanced security solutions such as Leargas Security XDR. This potent platform, built on the robust Zeek framework, offers an all-in-one approach to securing IT and OT environments, providing vital insights and capabilities that help businesses stay ahead of potential threats. This article will delve into the significance of Zeek-based solutions like Leargas Security XDR with an emphasis on OT protocol analysis including DNP3, Modbus, and S7.
Continue readingRevolutionizing Energy Cooperatives: The Value of Leargas Security XDR
As the globe becomes progressively dependent on digital systems and automation, cybersecurity has evolved into a pressing issue for all organizations. This trend is not just applicable to major corporations or tech firms; it is equally relevant to entities like energy cooperatives. Given their key responsibility in delivering vital services to communities, these cooperatives cannot afford to overlook the importance of robust cybersecurity measures.
Continue readingLeveraging CIRCL’s AIL Framework and Leargas Security XDR Platform for Effective Breach Discovery and Management
As the digital landscape expands, so does the complexity and magnitude of cybersecurity threats. This shift has led to the development of sophisticated cybersecurity tools designed to detect, manage, and respond to potential security breaches. Two such tools making waves in the cybersecurity field are the Computer Incident Response Center Luxembourg (CIRCL) Analysis Information Leak (AIL) framework and the Leargas Security Extended Detection and Response (XDR) platform.
Continue readingThe Perils of Threat Intelligence Feed Poisoning: The Importance of Proper Curation and Validation of Artifacts
As organizations adapt to the ever-changing cyber threat landscape, they increasingly depend on threat intelligence feeds to remain informed about the latest malicious activities and safeguard their digital assets. These feeds provide real-time, actionable information on a variety of cyber threats, encompassing elements such as IP addresses, domains, malware hashes, and email addresses. However, the very resource designed to protect an organization can also become its Achilles’ heel when threat actors poison these feeds, potentially compromising networks and systems. In this blog post, we delve into the significance of proper curation and validation of artifacts as a means to counter the risks linked to threat intelligence feed poisoning.
Continue readingZeek vs NetFlow: Why Léargas chose Zeek

As organizations continue to rely more on networked systems for critical operations, the need for efficient and effective network traffic analysis solutions becomes increasingly important. Two popular solutions for network traffic analysis are Zeek and Netflow, and many organizations are faced with the challenge of choosing between the two. In this blog post, we will take a closer look at each solution and explore why we are proudly built on Zeek.
What is Zeek?Zeek is a powerful and flexible open-source network security monitoring tool that provides a rich set of features for network traffic analysis. Zeek operates by capturing network packets and creating logs of network activity in real-time. These logs provide detailed information about network connections, protocols, and other relevant data, making it an ideal solution for security professionals who need to quickly identify security threats and respond to incidents. What is Netflow?
Netflow is a network traffic analysis protocol that was developed by Cisco Systems. Netflow provides a method for collecting information about network traffic and analyzing it to identify trends, anomalies, and other important information. Unlike Zeek, which focuses on analyzing network packets, Netflow focuses on analyzing network flow data, which is a high-level view of network activity. Netflow is well-suited for organizations that want to get an overview of network traffic patterns without getting into the technical details of packet analysis. Zeek vs Netflow: Pros and Cons
Zeek and Netflow each have their own strengths and weaknesses, and the solution that is best for you will depend on your specific needs and requirements.
Pros of Zeek:
- Network traffic analysis and inspection
- Intrusion detection and threat hunting
- Integrated Threat Intelligence
- Embedded File Extraction and Analysis
- Protocol analysis and decoding
- Flexible logging and reporting
- Customizable and extensible scripting
- High-performance and scalability
- Integration with other security tools
- Advanced analytics and data visualization
- Flexible deployment options (e.g. standalone, cluster, cloud)
Cons of Netflow:
- Limited in terms of the data it provides compared to Zeek
- May not provide enough detail for advanced network security analysis
- Does not provide real-time analysis
Choosing between the Zeek-based, Léargas Security platform over Netflow-based platforms for network traffic analysis is an easy decision.
If you’re looking for a solution that provides a rich set of features for network traffic analysis, real-time analysis of network packets, and the ability to identify security threats and respond to incidents quickly, then the Zeek-based, Léargas Security is the solution for you.
With the right solution in place, you can ensure that your network is secure and that you have the information you need to quickly respond to security incidents.
Léargas has always been about providing “Insight”. Now, it fights for the world!
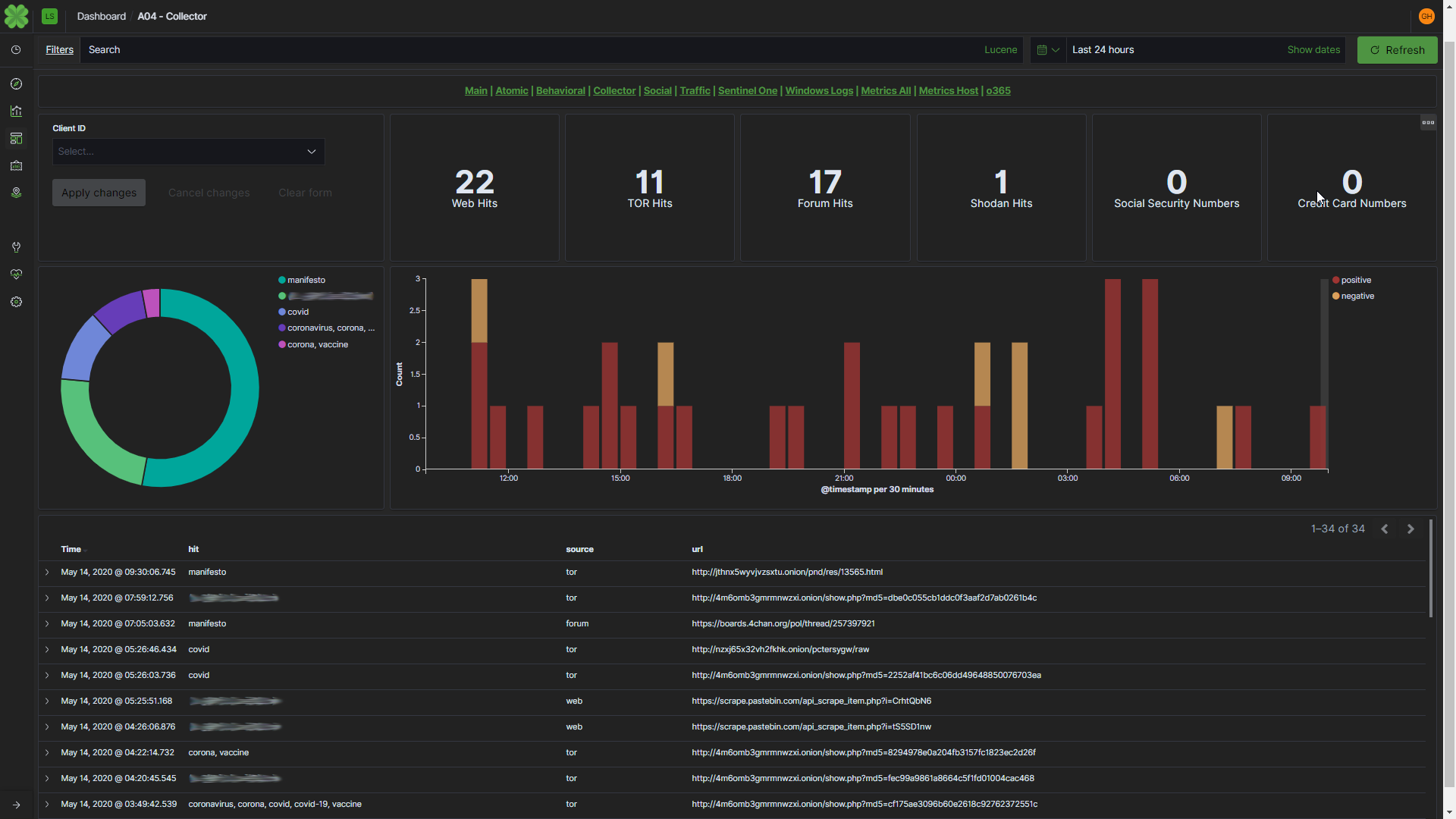
Léargas has always been about providing “Insight”. Now, it fights for the world!
Global events such as the Coronavirus (COVID-19) make all of us targets for cybercriminals. It could be in the form of phishing emails or new targeted scams, these tactics are meant to take advantage of individuals who are understandably concerned about their health and safety of their family during this challenging time.
Additionally, it targets companies that have effectively turned their infrastructure “inside-out” to provide all of the necessary services and data for their now remote-workers to perform at their best. That means weakened firewall rules, mission-critical servers connected to the Internet, and no multi-factor authentication.
This pandemic is challenging for all of us. We all need to adapt to this new reality and look out for one another any way we can. Our mission with Léargas has always been to protect people against threats at the intersection of cyber and the physical world, and this disaster has provided us with the motivation to find new ways to help.
As with any new endeavor, knowledge is key, so we began ingesting atomic indicators around COVID-19/Coronavirus and converting them into an actionable data set for the mitigation of COVID-related digital threats.
Immediately, we found an increase in malicious activity using COVID-19 as a lure to commit cybercrimes by offering urgent information in phishing emails, selling fake “vaccines” and numerous other scams. (Example is shown above)
We remain committed to keeping our clients safe during this pandemic. To that end, we have created a package of detections related to COVID-19 based attacks, which consists of known threat actors, attack methodologies, and how they’re exploiting COVID-19. If you are a Managed Services Partner or have a subscription to Léargas, there is nothing you need to do. The package was deployed and you will receive pertinent alerts as necessary.
Should you not be a subscriber, please reach out to us for more information on gaining access to these preventative measures.
Lastly, we want to provide some additional recommendations:
Recommendations for Our Clients:
Security always starts with the basics. If you aren’t using Léargas, make sure your systems are patched and IDS/IPS signatures and associated files are up to date. Attackers rely heavily on unpatched and out-of-date network configurations.Keep applications and operating systems running at the current released patch level. If you aren’t sure how to do this, reach out. One of our engineers will share some helpful information to assist you.
Leverage Multi-Factor Authentication! We see more companies breached each day due to the lack of multi-factor authentication than any other attack strategy. With hundreds of data breaches a year, we don’t expect this to decline.
Regrettably, in times like these when so many of us are coming together, there are still a few that will try to tear us apart. Be Aware, keep alert, stay strong, stay together, but stay 6 feet apart, for now.
-PK