Correlation and Enrichment: Office365 and Endpoint Security
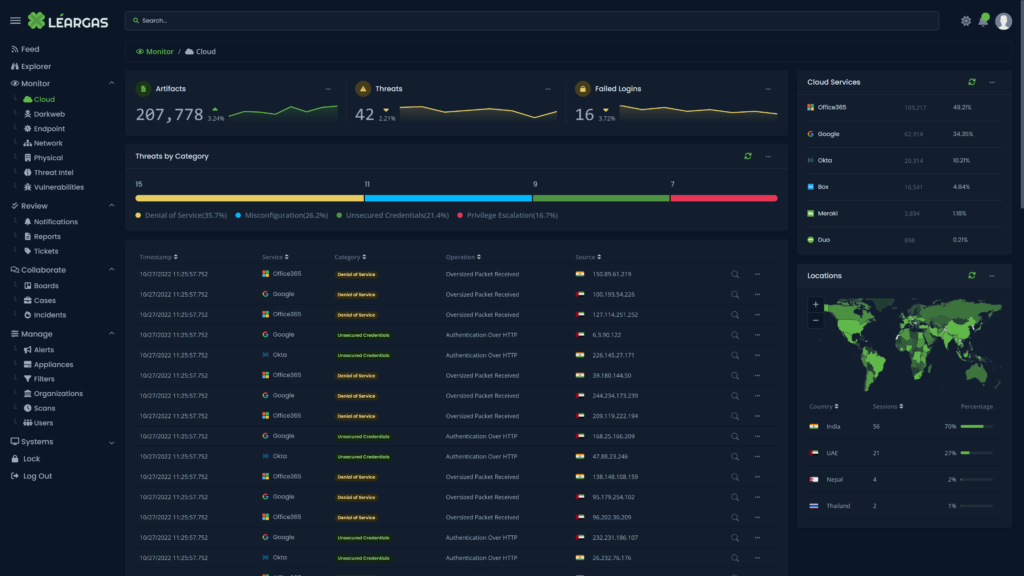
As organizations increasingly rely on cloud-based services such as Office 365 for their productivity and collaboration needs, it’s critical to understand the importance of correlating logs from both the cloud service and the endpoint devices. This correlation can provide a comprehensive view of the activities taking place within the organization and help ensure the security and compliance of sensitive information, no matter where the endpoint might be.
One of the main benefits of correlating Office 365 and Endpoint Security logs is that it can help identify suspicious or malicious activity. For example, if a user’s endpoint device shows signs of a security breach, geographically-impossible authentication attempts, or attacks such as a virus or malware event, the corresponding Office 365 logs can provide valuable information on what data may have been accessed or exfiltrated.
The Léargas Security platform automatically correlates the data from the sources into single searches and alerts.
Additionally, correlating Office 365 and Endpoint Security logs can also help organizations identify compliance violations, such as unauthorized access to sensitive information. With the right tools, organizations can quickly identify when a user has taken actions that violate their data protection policies, such as downloading confidential data onto a personal device or sending sensitive information to an unauthorized email recipient.
Moreover, correlating logs can help improve incident response time. In the event of a security incident, having a comprehensive view of the activities that took place can help organizations quickly identify the source and scope of the problem, enabling them to respond and resolve the issue more efficiently.
Here are the Top 10 reasons for automatically correlating Office 365 and Endpoint Security logs:
- IMPROVED VISIBILITY INTO USER ACTIVITY: Correlating logs provides a comprehensive view of what users are doing within the organization, including access to sensitive information and email correspondence, regardless of location and time.
- DETECTING SUSPICIOUS OR MALICIOUS ACTIVITY: Correlating logs can help identify potential security threats and unauthorized access to sensitive data.
- IMPROVING INCIDENT RESPONSE TIME: Having a comprehensive view of activities can help organizations quickly identify the source and scope of security incidents, allowing them to respond more efficiently.
- ENSURING COMPLIANCE WITH INDUSTRY REGULATIONS: Organizations can use log data to demonstrate compliance with regulations such as GDPR and HIPAA.
- AUDITING AND COMPLIANCE REPORTING: Log data can provide valuable insights for auditing and compliance reporting, helping organizations ensure that their security and privacy practices are up to standards.
- PROTECTING SENSITIVE DATA: Correlating logs can help organizations identify when sensitive data is being accessed, downloaded, or sent to unauthorized recipients, allowing them to take appropriate action to protect it.
- DETECTING ENDPOINT SECURITY BREACHES: Endpoint devices are a common target for attackers, and correlating logs can help organizations identify when a device has been compromised and what data may have been accessed.
- IDENTIFYING UNUSUAL USER BEHAVIOR: Correlating logs can help organizations identify when users are engaging in suspicious or unusual behavior, allowing them to take appropriate action to mitigate potential threats.
- DETECTING DATA EXFILTRATION: By tracking user activities, organizations can identify when sensitive data is being exfiltrated and take appropriate action to prevent it.
- ENHANCING SECURITY AND PRIVACY: By correlating logs, organizations can gain a better understanding of their security and privacy practices and take appropriate steps to improve them.
Finally, correlating Office 365 and Endpoint Security logs can also provide valuable insights for auditing and compliance reporting. Organizations can use the data from these logs to demonstrate their compliance with industry regulations and standards, such as GDPR and HIPAA, by providing a detailed view of their security and privacy practices.